In the current dynamic landscape of business, the most significant risks often arise from internal sources. Insider threats, whether they stem from malicious intent or unintentional actions, can severely impact your organization’s reputation, financial stability, and overall security posture.
But what exactly are these threats, and how can you safeguard your business against them? Let's dive into the risks and explore the tools and strategies that can help you stay protected.

Understanding Insider Threats: What Are They?
Insider threats refer to risks posed by employees, contractors, or business partners who have inside access to your company's systems, data, and networks. These threats can be categorized into two types:
1. Malicious Insider Threats: These are individuals who intentionally exploit their access to cause harm, steal sensitive data, or disrupt operations. Their motives can vary from financial gain to corporate espionage or revenge.

2. Accidental Insider Threats: Not all insider threats are intentional. Sometimes, employees unintentionally expose sensitive information, fall victim to phishing attacks, or misconfigure systems, leading to data breaches.

Both types of insider threats can be equally damaging, and businesses need to be vigilant to detect and prevent them.
The Risks of Insider Threats
The impact of an insider threat can be catastrophic, affecting your business in several ways:
- Data Breach: Insider threats can lead to the exposure of confidential information, including customer data, trade secrets, and intellectual property.
- Financial Loss: The financial repercussions can be severe, from regulatory fines to loss of revenue due to disrupted operations.
- Reputation Damage: A data breach or security incident can tarnish your brand’s reputation, leading to a loss of trust among customers and partners.
- Legal Consequences: Businesses may face legal actions from customers, partners, or regulatory bodies if it’s proven that they failed to protect sensitive data.
Mitigating Insider Threats: Strategies to Keep Your Business Safe
To protect your business from insider threats, it’s essential to implement a combination of policies, education, and technology. Here’s how you can do it:
1. Establish Clear Security Policies: Clearly define and communicate your company’s security policies. Make sure employees understand what’s expected of them regarding data handling, access control, and reporting suspicious activities.

2. Conduct Regular Training: Regularly train your employees on cybersecurity best practices, including recognizing phishing attempts, safeguarding passwords, and the importance of following security protocols.

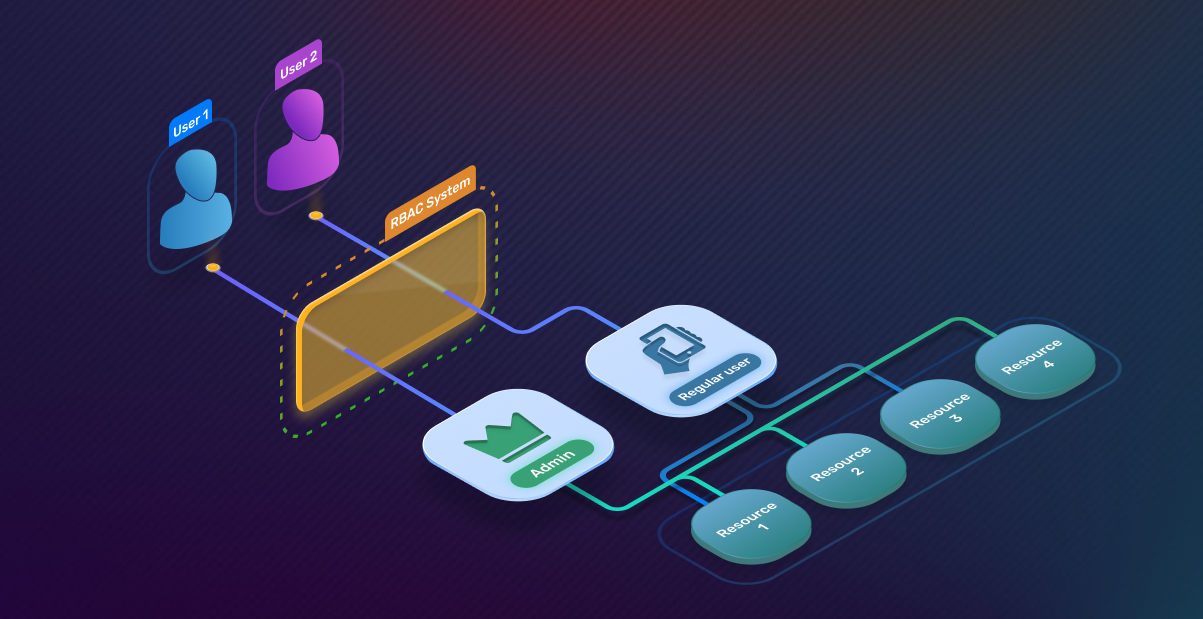
3. Implement Role-Based Access Control (RBAC): Limit access to sensitive data and systems based on an employee’s role within the company. This minimizes the chances of unauthorized access.
4. Monitor Employee Behavior: Use monitoring tools to detect unusual or suspicious activities, such as unauthorized access to sensitive data, downloading large files, or logging in at odd hours. Regular audits can also help identify potential insider threats early on.

5. Encourage a Security-First Culture: Foster a workplace culture that prioritizes security. Encourage employees to report any suspicious behavior or potential vulnerabilities without fear of retribution.

Tools for Monitoring and Detecting Insider Threats
The right tools can make all the difference in detecting and preventing insider threats. Among these tools, SentryPC stands out as a comprehensive solution for businesses looking to monitor and protect their systems from insider threats.
SentryPC offers robust monitoring capabilities that allow you to track employee activity, detect unusual behaviors, and enforce security policies. With features like real-time alerts, detailed activity logs, and remote access, SentryPC helps you stay one step ahead of potential threats.
Incorporating tools like SentryPC into your security strategy not only helps you detect threats but also provides you with the insights needed to take swift action. By keeping a close eye on what’s happening within your network, you can protect your business from the inside out.
When it comes to protecting your business from insider threats, SentryPC is your go-to solution. It’s not just about monitoring; it’s about having the power to detect and respond to potential threats before they escalate.
With SentryPC, you can:
- Monitor Employee Activity: Keep track of user behavior, applications accessed, and websites visited.
- Detect Unusual Activities: Get alerts on suspicious behaviors that could indicate an insider threat.
- Enforce Security Policies: Ensure compliance with company policies through customizable restrictions and controls.
Don’t wait for a security breach to take action. Start protecting your business today with SentryPC.
Explore the benefits of SentryPC and safeguard your business from insider threats.
1. How can I improve website load speed?
Use optimized images, enable browser caching, utilize a content delivery network (CDN), and minimize code (HTML, CSS, JavaScript). Fast load times improve user experience and SEO rankings.
2. What is the role of mobile optimization in website success?
Mobile optimization ensures your site is user-friendly on smartphones and tablets, enhancing user experience and search rankings. Use responsive design and test across devices.
3. How do I improve website navigation?
Create a clear menu structure, use descriptive labels, and limit dropdown layers. Include a search bar for quick access, improving usability and reducing bounce rates.
4. How can keyword research help optimize my website?
Targeting the right keywords aligns your content with user search intent, boosting organic traffic. Use tools like Google Keyword Planner to identify valuable terms.
5. Why is secure hosting crucial for website performance?
Secure hosting protects your site from cyber threats, ensures uptime reliability, and improves user trust. Look for providers offering SSL certificates and robust security measures.