Remote work is no longer a trend—it's the new normal. While the flexibility of working from home has been a boon for employees, it has introduced a new set of challenges for businesses, particularly in terms of cybersecurity.
With employees accessing company data from various locations and devices, the risk of cyberattacks has significantly increased. Ensuring robust cybersecurity in remote work environments is not just an option; it's a necessity.

The Importance of Monitoring Employee Activity
In a traditional office setting, maintaining oversight of employee activity is relatively straightforward. However, in a remote work environment, this becomes much more complex. Businesses need to be vigilant to protect sensitive data from being exposed, whether intentionally or unintentionally. Monitoring employee activity is crucial for several reasons:
1. Preventing Data Leaks: Without proper monitoring, employees might unknowingly or deliberately share sensitive information through unsecured channels.
2. Ensuring Productivity: With the blurring of personal and professional spaces, employees may get distracted. Monitoring helps ensure that work time is spent productively.
3. Detecting Insider Threats: Not all threats come from outside the organization. Monitoring can help identify unusual behaviors that might indicate an insider threat.
4. Compliance and Legal Protection: Many industries have strict compliance requirements regarding data protection. Monitoring ensures that your business adheres to these regulations, safeguarding against potential legal repercussions.

Best Practices for Cybersecurity in Remote Work
Securing your remote workforce requires a multifaceted approach. Here are some best practices that every business should implement:
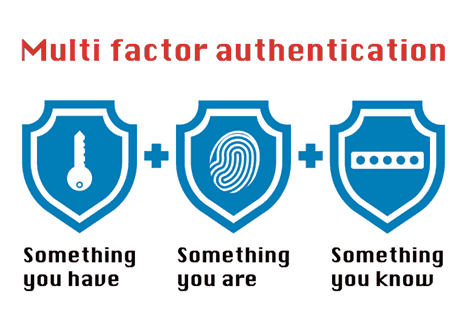
1. Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security, making it harder for unauthorized users to access company systems. Even if an employee's password is compromised, the attacker would still need a second form of verification to gain access.
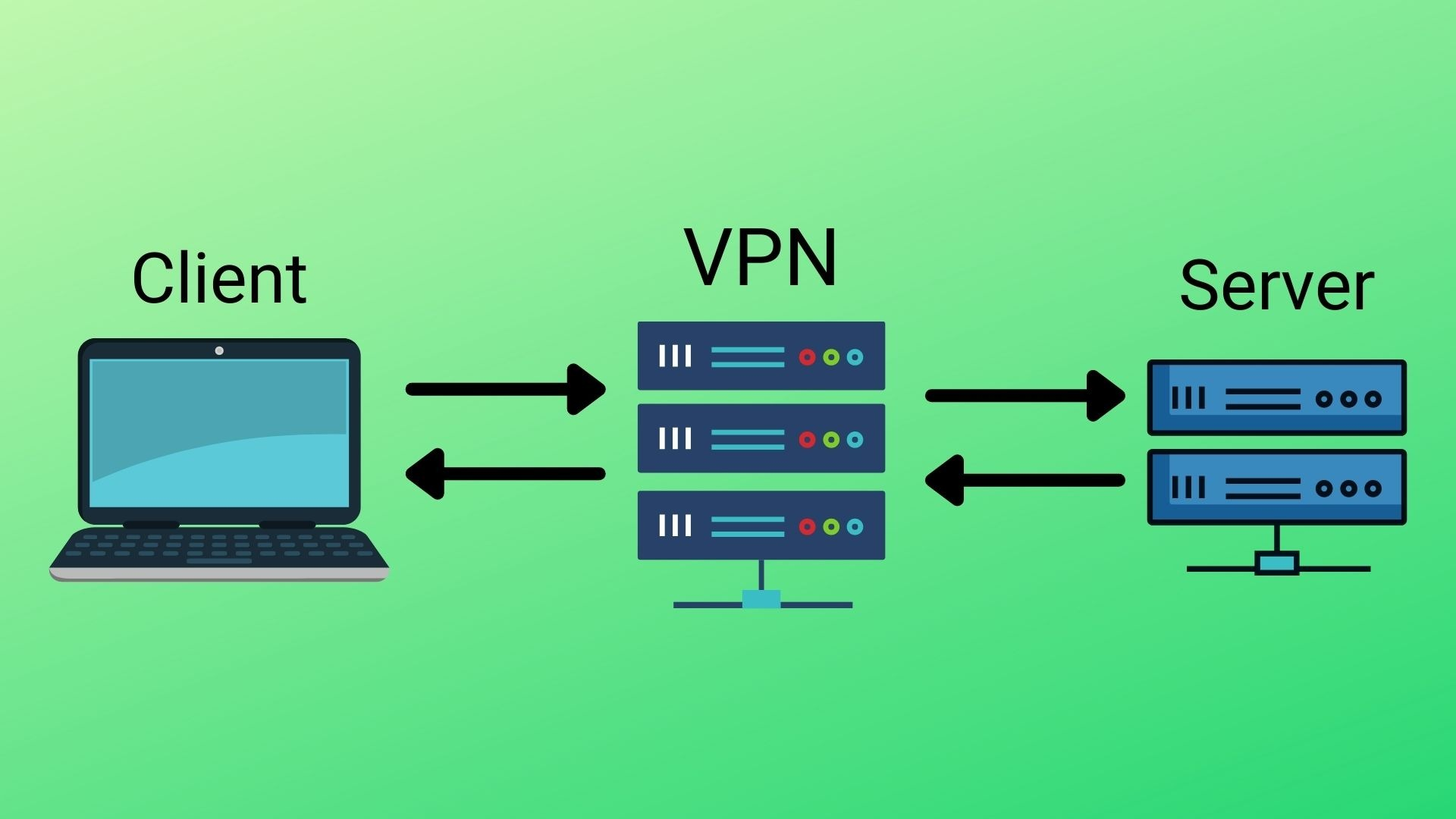
2. Use VPNs for Secure Connections
Virtual Private Networks (VPNs) ensure that all data transmitted between employees' devices and the company network is encrypted. This is especially crucial when employees are using public or unsecured Wi-Fi networks.
3. Regularly Update Software and Systems
Outdated software is a common entry point for cyberattacks. Ensure that all systems, including employees' devices, are regularly updated with the latest security patches.

4. Conduct Regular Cybersecurity Training
Employees are often the weakest link in cybersecurity. Regular training sessions can educate them on the latest threats, how to recognize phishing attempts, and the importance of following company security protocols.
5. Implement Data Encryption
Encrypting data ensures that even if it is intercepted, it cannot be read by unauthorized parties. This applies to both data at rest (stored data) and data in transit (data being sent).

6. Monitor and Control Employee Access
Not all employees need access to all company data. Implement role-based access controls to limit access to sensitive information based on an employee's role within the company.
SentryPC: A Solution to Secure and Manage Remote Work Environments
In the ever-evolving landscape of remote work, businesses need tools that not only monitor employee activity but also enhance cybersecurity. SentryPC is a powerful software solution designed to help businesses manage and secure their remote work environments effectively.
Benefits of Using SentryPC
- Comprehensive Activity Monitoring: SentryPC allows you to monitor all employee activity, ensuring that work is done efficiently and securely.
- Content Filtering and Blocking: Prevent access to harmful or distracting websites and applications, keeping your employees focused and your data safe.
- Time Management Tools: Easily manage how much time employees spend on specific tasks or applications, ensuring optimal productivity.
- Advanced Analytics and Reporting: Gain insights into employee behavior and identify potential security risks with detailed reports and analytics.
- Stealth Operation: SentryPC operates in stealth mode, ensuring that your monitoring efforts do not interfere with employee performance.
Investing in SentryPC can help your business maintain a secure and productive remote work environment. Explore SentryPC to learn more about how it can benefit your organization and keep your data safe. Start securing your remote workforce today with a solution that's trusted by businesses worldwide.